
Leverage Streebo’s Expertise to guard your applications!
Ensure your Application Security Transformation meet regulatory compliance ExploreDiscover vulnerabilities of your system and keep data and
resources secure with Streebo’s testing services

The emergence of the digital channel has led to connecting everyone across the globe. This has led to increased dependency of consumers on online channels leading to increased data share and transactions. Processing these transactions may lead to malicious activities if the environment is not secure. These minor and major breaches may lead to loss of customer’s trust and ultimately revenue.
A robust approach is necessary for keeping apps, website and other digital assets secure as it receives and stores a lot of data from customers, clients and partners.
A robust approach is necessary for keeping apps, website and other digital assets secure as it receives and stores a lot of data from customers, clients and partners.
Some of the recent surveys shows
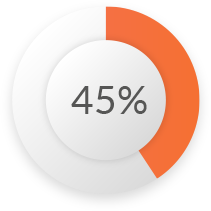 Of the organizations will spend more on application security in the next 12 months
Of the organizations will spend more on application security in the next 12 months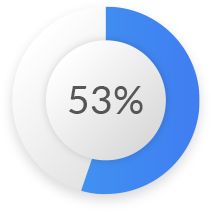 Of respondents say DDOS, SQL injections and XML bombs are the brightest API security concerns
Of respondents say DDOS, SQL injections and XML bombs are the brightest API security concerns
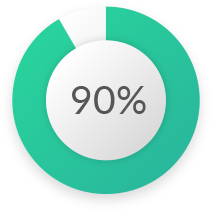 Of web apps with vulnerabilities are due to lack of security
Of web apps with vulnerabilities are due to lack of securityWhy Security Testing?

System testing, in the current scenario, is a must to identify
and address web application security vulnerabilities.
By getting your app tested the following can be avoided:
By getting your app tested the following can be avoided:
- Mitigate unplanned website downtime
- Unauthorized access
- System vulnerability risk
- Sensitive information leakage
- Expenditure in recovering from damage
- Legal implications and fees
- Lack of customer trust
- Leakage of Customer’s online data that impact to
- revenue generation/collection
Security Testing Methodology

Streebo’s Offering in Security Testing
- Server Information gathering
- Website Information gathering
- HTTP communications
- API Calls Leaks
- Device Info Leaks
Web application security Parameters
- Server Information gathering
- Website Information gathering
- Session Cookie Hijacking & Management
- Server/OS information Leakage
- Missing Security Headers
- XSS attacks
- SQL & XML Injection
- Session Management
- Cookie Management
- LDAP injection
- Upload unexpected File Types
- Email Bombing and Spamming
- Sensitive Data Exposure
- Missing Functional Level Access Control
- Invalidated Redirects and Forwards
- Configuration and Deployment Management Testing
- Integrity Checks
- Cryptography
- Business Logic Data Validation
- API Attacks
- Error Handling
- System Exploitation
- Highlight the Risk of vulnerabilities
- Detail Reporting of each parameters
- Recommendations
Android Penetration testing parameters list
- HTTP communications
- API Calls Leaks
- Device Info Leaks
- Unencrypted SQLite DB
- Log files
- Shared Prefs data check
- Self-Signed Certificate
- SSL Check
- User’s session ID Hijacking
- Copy/Paste buffer caching
- Logging Check
- Clear text authentication leak
- Authentication Token Leak check
- XSS (cross site scripting)
- SQL injection
- Reflected XSS in URL parameter
- Code injection
- Code Analysis
- Hard-coded Sensitive Information Check
- Malware Analysis




